Actions
Bug #4385
openhttp_method parsing error
Status:
New
Priority:
Normal
Assignee:
-
Target version:
-
Affected Versions:
Effort:
Difficulty:
Label:
Description
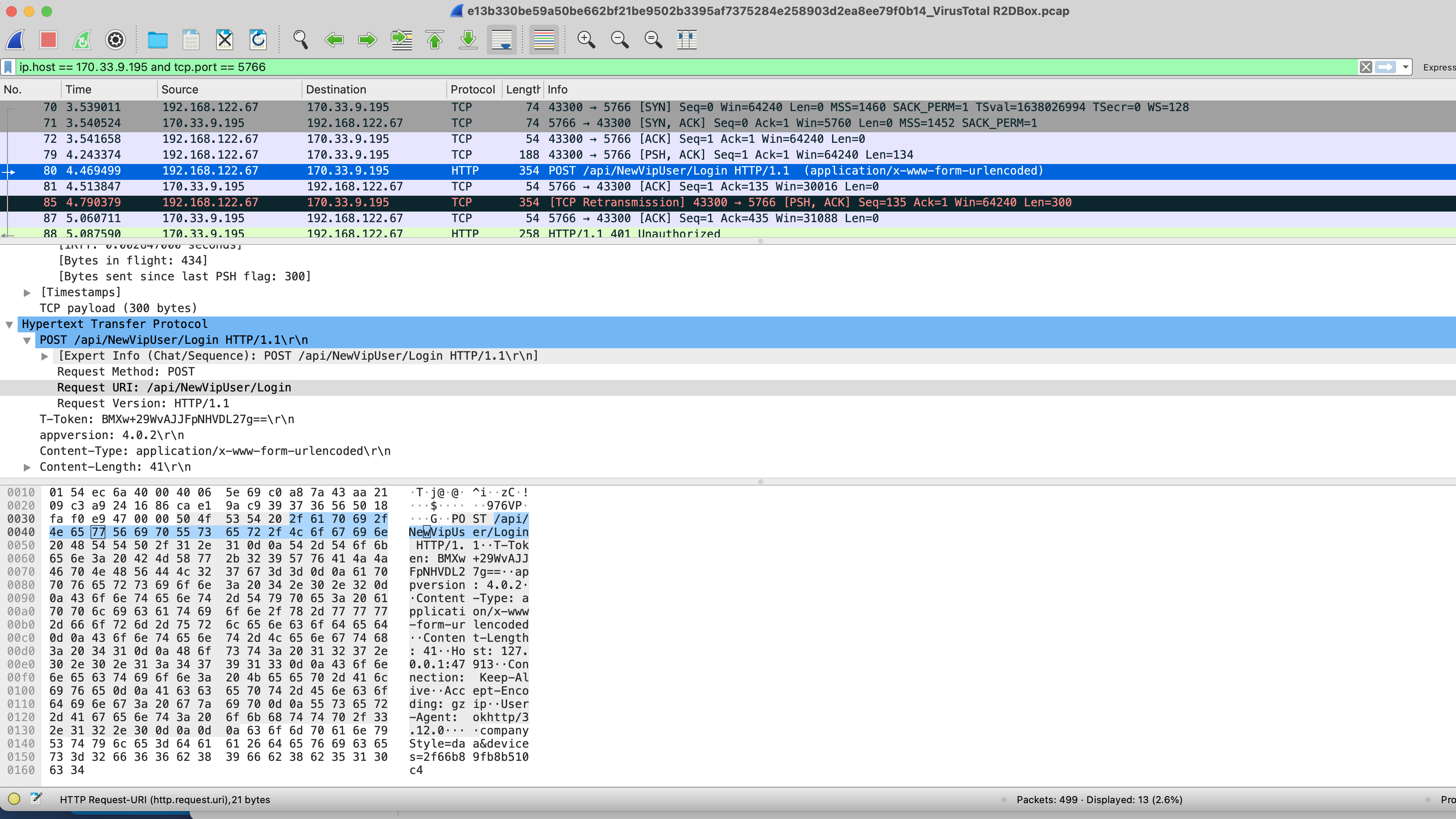
Using Suricata 6.0.2 I've observed this http_method parsing error.
It might be related to TCP re-transmission of the HTTP POST.
{
"timestamp": "2021-03-04T14:16:28.366586+0000",
"event_type": "alert",
"src_ip": "192.168.122.67",
"src_port": 43300,
"dest_ip": "170.33.9.195",
"dest_port": 5766,
"proto": "TCP",
"app_proto": "http",
"app_proto_ts": "failed",
"alert": {
"action": "allowed",
"gid": 1,
"signature_id": 2221029,
"rev": 1,
"signature": "SURICATA HTTP URI terminated by non-compliant character",
"category": "Generic Protocol Command Decode",
"severity": 3
},
"http": {
"hostname": "127.0.0.1",
"url": "\\xa9\\xb8��\\xc7*����������������=\\xfc�\\xaa\\xe5\\xaa\\x93z1+$\\xbc\\xe0\\x87\\xce\\xbf���8������&\\xdf\\x8bJ\\xe0\\xe3c�\\xd39Y\\xe08./�\\x92\\x8b��\\x8eku\u000bY�f\\xff\\xd0\\xe2\\xa5lv\\xf9x&3?\\x8f\\x9aL\\xefv\\xf2\\xc7��\\xbaPOST",
"http_user_agent": "okhttp/3.12.0",
"http_method": "V\\xf2\\xb4���N��\\x86��\\xb7\\xe5ZF������\\xab\\xda\\xa5\\xf2#)��`@\\xeb\\xb8��r",
"protocol": "/api/NewVipUser/Login HTTP/1.1",
"status": 401,
"http_port": 47913
},
"flow": {
"pkts_toserver": 6,
"pkts_toclient": 4,
"bytes_toserver": 1078,
"bytes_toclient": 440,
"start": "2021-03-04T14:16:26.816060+0000"
},
"metadata": {
"flowints": {
"http.anomaly.count": "2",
"applayer.anomaly.count": "1"
},
"flowbits": [
"FB180732_0",
"http.dottedquadhost"
]
}
},
Files
Updated by Philippe Antoine about 3 years ago
This seems due to the packet 79 which contains some binary non-HTTP
And the server answers 401 to this binary non-HTTP
Do you have a web server that will accept this request ?
Updated by Karl H about 3 years ago
Philippe Antoine wrote in #note-1:
This seems due to the packet 79 which contains some binary non-HTTP
And the server answers 401 to this binary non-HTTPDo you have a web server that will accept this request ?
This particular request was done in a sandbox analysis within a virtual machine.
Actions