Bug #4615
closedMultiple identical request headers will not be detected by signatures, causing attacks to bypass
Description
I write the signature: alert http any any -> any any (msg:"Header Attack";flow:established,to_server;content:"TEST:|20|evil";nocase;http_header;sid:1;rev:1;)
Start suricata listening network card: `suricata -c suricata.yaml -s signatures.rules -i enp0s3`
I send the following request message: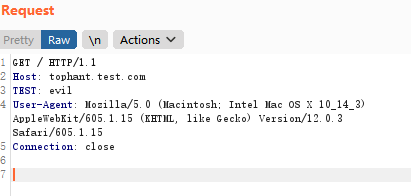
The attack was discovered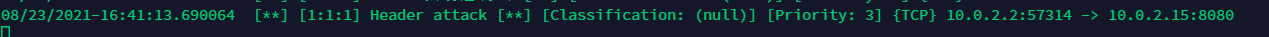
But when I bypassed the attack through the same request header, Suricata did not detect the attack payload.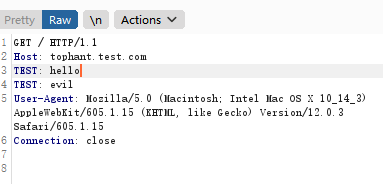
This will cause the attack payload to bypass Suricata. Similarly, many exploits passed the attack payload through the HTTP request header. This bypass method will cause a lot of trouble.
Best Regards.
Files
Updated by Jiacheng Zhong over 2 years ago
Hello, I found that my keyword was used incorrectly . This issue can be closed. Thanks :)
Updated by Jeff Lucovsky over 2 years ago
- Status changed from New to Closed
- Target version changed from 6.0.2 to TBD
Closed by request of reporter.
Updated by Philippe Antoine over 2 years ago
Thanks, so closing
For reference, https://suricata.readthedocs.io/en/suricata-6.0.3/rules/http-keywords.html#http-header-and-http-header-raw about headers normalization
Updated by Victor Julien over 2 years ago
- Tracker changed from Security to Bug
- Status changed from Closed to Rejected
- Target version deleted (
TBD) - Severity deleted (
MODERATE)